- About D-Link
- Products and Services
- ESG
Sustainable Development
Sustainable Supply Chain
Sustainable Workplace
For Stakeholders
- Investor Relations
- News Room
- Careers
Home > ESG > Governance > Information Security Management
Home > ESG > Governance > Information Security Management
Information Security Management
Home > ESG > Governance > Information Security Management
Information Security Management
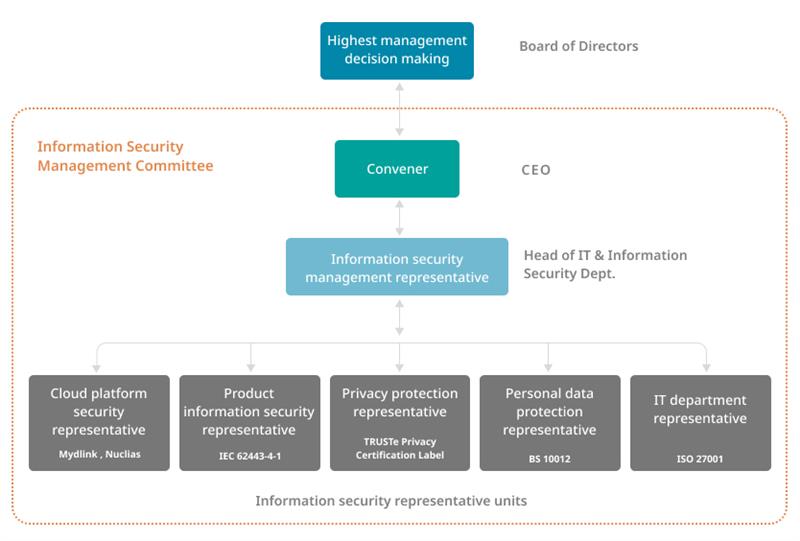
Information Security Organization and Structure
In order to fully manage information and communication security, D-Link has established the “Information Security Management Committee” in 2021. The President shall act as the convener to supervise the information security policies of the entire company. The Committee references the ISO/IEC 27001:2022 information security management system international standards and the public company internal control system establishment guidelines. The IT and Information Security Department serves as the dedicated information security unit and the department head shall act as the information security management representative to coordinate the formulation, execution, risk management, and compliance audit of information security and protection related policies. Each information security related unit (product, personal data, privacy, etc.) shall appoint an information security representative to regularly convene information security meetings. They shall discuss information security policies and other material issues related to information security, as well as supervise the execution of the company’s information security operations and the effectiveness of the information security risk management mechanisms. The execution results of the information security management operations and systems of the entire information security management organization shall be reported to the Board of Directors regularly.

D-Link Information Security Organization
Information Security Management Strategy
D-Link’s Board of Directors has passed the “Information Security Management Policy” on February 22, 2022. The confidentiality, integrity, availability, and legality of information assets are reviewed regularly every year.
Information Security for Systems
D-Link has passed the “ISO/IEC 27001:2022 Information Security Management System (ISMS)” international certification. The effective period of the current certification is from October 16, 2020, to October 15, 2026. Through the introduction of the ISO/IEC 27001 Information Security Management System, we have strengthened our response and handling capabilities for information security incidents to protect the security of the company’s and customers’ information assets.

Product Security
D-Link follows strict security regulations throughout the product development process to ensure that all products pass the relevant security tests and there are no exploitable vulnerabilities before production. To maintain a high level of product security, D-Link conducts annual internal audits and commissions independent audits by external third-party security verification agencies every two years. Additionally, D-Link performs regular security audits on its partners to rigorously ensure the quality of its product security.

Product Security
D-Link has passed the “IEC 62443-4-1:2018 Secure Product Development Lifecycle Requirements” international certification in 2020. The effective period of the current certification is from November 30, 2020, to November 29, 2025. The requirements have been introduced in product lifecycles from product design to development and testing, ensuring compliance with the security standards.

Product Security
To address the upcoming EU Radio Equipment Directive (CE RED) cybersecurity requirements under Article 3.3 (d), (e), and (f), which will take effect in 2025, D-Link proactively launched a dedicated project in mid-2022. In advance of the enforcement date, we revised product security specifications in alignment with the ETSI EN 303 645 standard.
In May 2023, D-Link’s AQUILA PRO AI M30 AX3000 Wi-Fi 6 Dual-Band Router became the first product in Taiwan to receive the EN 303 645 certification. Since then, multiple D-Link wireless products have successfully obtained the same certification.
Furthermore, following the release of the EU’s latest EN 18031 security standard in early 2025, D-Link immediately initiated the certification process. The latest AQUILA PRO AI M95 BE9500 Wi-Fi 7 Tri-Band Mesh Router successfully passed the new cybersecurity requirements of the EU RED, becoming the first in Taiwan’s networking industry to be certified. The product was awarded the CE RED Type Examination Certificate (TEC) by the internationally recognized certification body Nemko—marking a significant milestone for D-Link and the industry in entering a new era of cybersecurity compliance.

Personal Data Protection
D-Link has passed the “BS 10012:2017 Personal Information Management System (PIMS)” international certification in 2021. The effective period of the current certification is from December 1, 2021, to November 30, 2027. All procedures and applicable documents related to the standards comply with the EU General Data Protection Regulation (GDPR) requirements.
I. Policy Scope and Governance Structure
D-Link is committed to establishing a comprehensive privacy protection framework to ensure that all personal data collected, processed, and used complies with applicable international standards and local regulatory requirements.
The Company has established a Personal Data Protection Policy as the highest guiding principle for personal data protection and management.
Scope of Application:
The policy applies to all business operations and information systems of the Company that involve personal information and is appropriately extended to relevant stakeholders (e.g., suppliers).
Responsible Unit:
A Personal Data Protection Task Force has been established and is directly supervised by the Chief Executive Officer.
Management Representative:
The Chief Legal Officer serves as the management representative and is responsible for the establishment, maintenance, and review of the personal data protection management system.
II. Integration of Risk Management and Compliance Mechanisms
The Company integrates personal data protection into its daily operations by conducting pre-emptive risk assessments and post-implementation audits, thereby establishing a multi-layered defense framework. Relevant measures are implemented in accordance with the Personal Data Protection Policy and related internal management procedures.
Risk Identification:
Risks and vulnerabilities associated with business operations and information systems of the Company that involve personal information are identified and assessed on a regular basis.
Violation Handling:
A zero-tolerance policy is adopted. Any violation of personal data protection regulations will be subject to disciplinary actions, in accordance with applicable rules and procedures.
Internal And External Audit:
Dedicated audits are included in the annual audit plan and conducted every year. In addition, the validity of the BS 10012 certification is maintained through the yearly verification by an accredited third-party certification body, thereby ensuring the continued effectiveness of control measures.

Privacy Protection
D-Link has obtained “TRUSTe Privacy Certification Label” international certification in March 2022. In order to implement privacy protections and commitments to security, D-Link has been working closely with the globally recognized data privacy management authority, TrustArc Inc., since 2014. TrustArc Inc. provides services such as privacy evaluations, certification, and monitoring tools. The external service website and related domains have passed the company’s audits and certification and have received the TRUSTe Privacy Certification Label.

Information Security Risk Management and
Continued Improvement Framework
D-Link has been cultivating network equipment and services markets for a long time. We place great importance on information security and the scope of our focus includes employees, organizations, supplier and operation related information, and software and hardware. D-Link complies with the ISO/IEC 27001:2022 Information Security Management System standards to formulate the information security policy. We have strengthened information security management to ensure that valuable information assets are protected from intentional or accidental internal and external threats, in order to maintain the confidentiality, integrity, and availability of data. Through the information asset and risk management procedures, we have established and are maintaining the company’s valuable information assets using the “Plan – Do – Check – Act” model. We ensure the continued operation of our business, reduce operational risks, enhance service quality, and ensure the consistent and effective implementation of all information security related policies, procedures, and operating guidelines during daily operations.

Specific Information Security Management Solutions
Information Security Protection and Controls
Network Security
Introduce advanced technologies to conduct computer scans and software updates, strengthen software firewalls and computer controls, and prevent the spread of computer viruses
Device Security
- Improve endpoint anti-virus and virus scanning mechanisms to prevent ransomware and malicious programs from entering the company
- Improve endpoint anti-virus and virus scanning mechanisms to prevent ransomware and malicious programs from entering the company
Web Application Security
- Improve endpoint anti-virus and virus scanning mechanisms to prevent ransomware and malicious programs from entering the company
Continue to strengthen security control mechanisms for applications and repair potential vulnerabilities
Access Control
Stipulate the user password management mechanism, network security service mechanism, and methods of internal network segmentation and external connection to manage remote work and protect network and information security
Password Key Management
- In order to ensure the system operations of the company and confidentiality of accounts, necessary passwords and keys are managed, in order to minimize the risk of leaks and appropriately protect D-Link’s sensitive information Option
Establishing the password policy defines the password strength rules and forces changing the password every three months.
Continuous Operation Management
D-Link shall establish operation continuity plans for important systems and implement annual drills to ensure continued operations
Information Security Incident Management
- In order to reduce the damage caused by information security incidents, information security incident reporting and handling procedures are established
Information Security Risk Review and Continuous Improvements
Education/Training / Promotion
- Strengthen employee vigilance against social engineering attacks through email and implement phishing email detection
- Regularly organize continued operation drills and improve employee information security awareness
Information Security Risk Management and Monitoring
Commission a third-party impartial inspection unit to regularly conduct information security evaluations on the company:
- ISO/IEC 27001:2022 Information Security Management System
- IEC 62443-4-1:2018 Secure Product Development Lifecycle Require
- BS 10012:2017 Personal Information Management System
External Threat Detection and Protection
Commission a third-party impartial inspection unit to regularly conduct vulnerability scanning and regularly collect external threat information. The information is used to perform risk assessments to strengthen external information security threat protection Option
We have joined the Taiwan Computer Emergency Response Team/Coordination Center (TWCERT/CC) to regularly collect external threat information and conduct risk assessments according to the information content. Information security personnel are responsible for confirming and tracking the handling results of the information to strengthen external information security threat protection Option


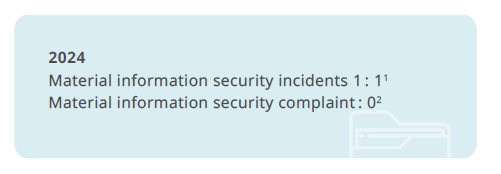
Information Security Incidents
In October 2024, the Company encountered a hacking attack on the server of an external web page; it was fortunate to have no damage to the rights and interests of customers, nor any disruption to the Company’s operations or other impacts. At the moment of an attack, the IT Department immediately blocked the connection to prevent the attack from spreading, activated all defense mechanisms, and invited technical experts from external information security companies to collaborate and comprehensively inventory and strengthen the information security detection and protection mechanism. Although no significant impact has been caused, the Company will continuously improve the security control of network and infrastructure to ensure information security.